Encryption
Encryption keys, plaintext and ciphertext
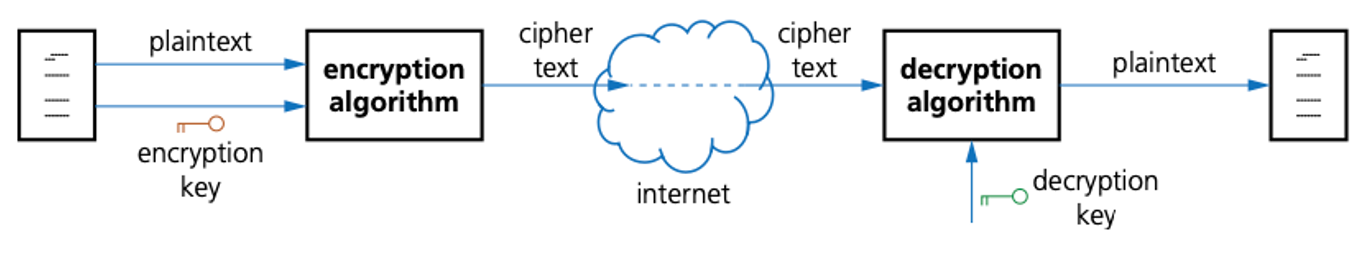
- The original data being sent is known as plaintext.
- Once it has gone through an encryption algorithm, it produces ciphertext.
- Note that, when encrypting text, block cipher is usually used.
- Here, the encryption algorithm is applied to a group of contiguous bits (for example, 128bits) rather than one bit at a time (which is known as stream cipher).
- With block cipher, each plaintext block is XORed with the previous ciphertext block and then encrypted – this is known as block chaining.
- This prevents identical blocks of plaintext producing the same ciphertext each time they are encrypted.
Symmetric encryption
- Symmetric encryption uses a secret key; the same key is used to encrypt and decrypt the encoded message.
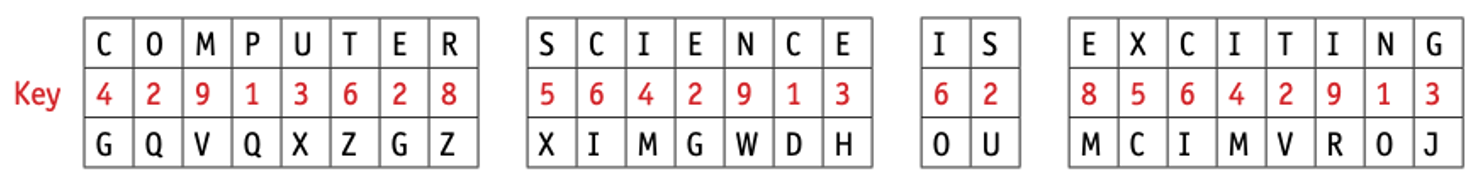
- Consider a simple system which uses 10-denary-digit encryption (which gives about 10 billion possibilities).
- Suppose our secret key is 4 2 9 1 3 6 2 8 5 6, which means each letter in a word is shifted across the alphabet +4, +2, +9, and so on, places.
- One issue with symmetric encryption is that both sender and recipient need to use the same secret key.
- This is a security risk here, since the sender has to supply the key to the recipient.
- This key could be intercepted.
- This is referred to as the key distribution problem.
Asymmetric encryption
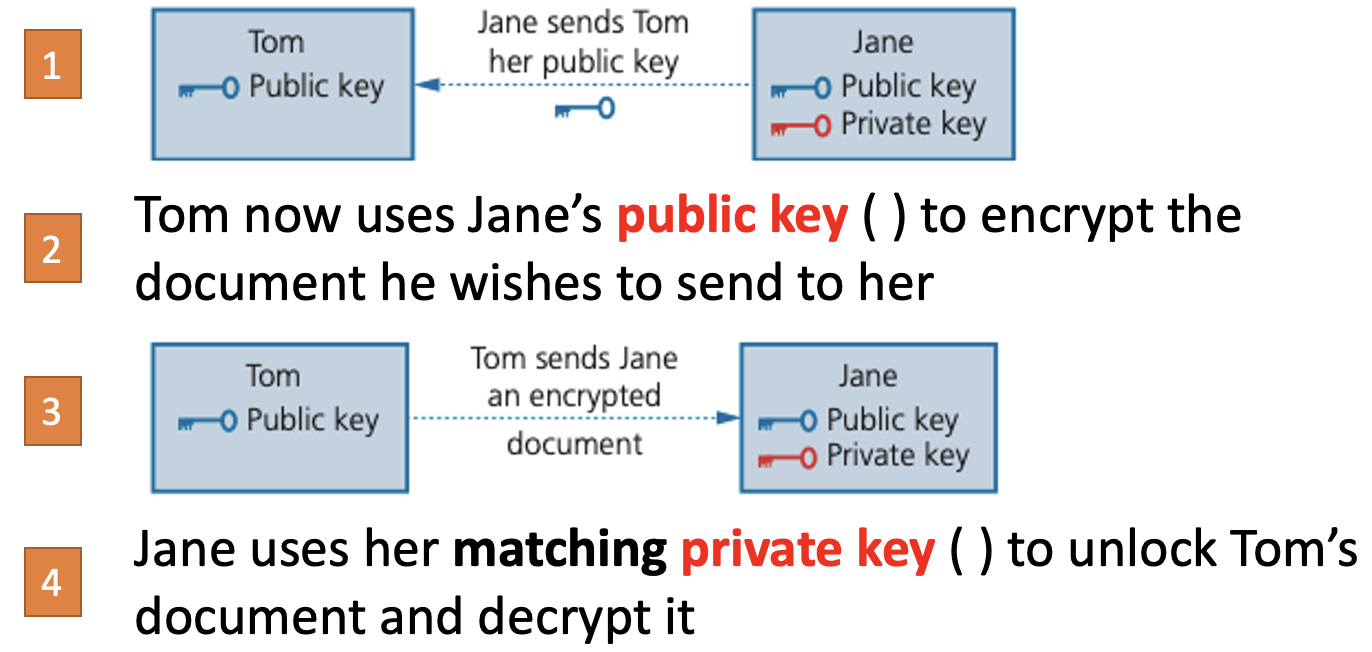
- Asymmetric encryption uses two keys – a public key, available to all users, and a private key, known to a specific person or computer.
- Suppose Tom and Meera work for the same company.
- Jane wishes to send a confidential document to Tom.
- Here’s how he could do it.